Net Protector Licence Key Generator
If NPAV is already installed in your system, then no need to install it again, you just have to renew the license key.
Net protector antivirus provides cyber security solutions for you and your buisness.npav protect your pc,mobile,laptop from viruses,ransomware,malware and keeps you safe from all cyber attacks. You will receive Net Protector license Key on your Email ID and Mobile Number. The Abluescarab Designs CD-Key Generator will help you generate random CD keys for use in your shareware products. You can choose letters, numbers, or both. You can also pick whether or not to use lowercase letters. Nba Live 2007 Serial Key Net Protector Antivirus Serial Key Download Wrc 3 Pc Game Serial Key Mac Ms Office 2018 Serial Key Malwarebytes Premium 3.4.5 Serial Key 2018 Fifa 18 Serial Key Generator Password.txt Serial Key Sage 50 Accounting Ca Fonelab Android Data Recovery Serial Key. By Mirrasoft Mirrakey is a Software License Key ActiveX DLL that is powerful and flexible. Mirrakey is a complete solution for generating license keys and validating licensed users with seamless.
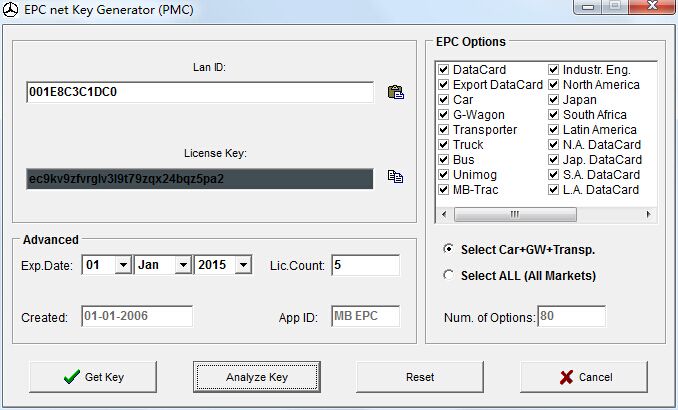
Net Protector License Key Generator Without Survey
Step 5: After filling all the information click on ONLINE button.
Your NPAV license is activated successfully, Your PC is secure now.
License Key Generator Online
| The Enigma Protector includes a wide range of unique features aimed at protecting executable files from illegal copying, hacking, modification, and analysis. The supported formats include almost all types of 32- and 64-bit executable files (exe, src, dll, ocx, bpl, etc.) and .NET files created using various development tools, such as MS Visual Studio C#/C++/VB/VB.NET, Borland Delphi/C++, FreePascal, MASM, TASM and others. The protected files can be run on all versions of Windows 95/98/ME/2000/XP/2003/Vista/2008/Seven/2012/8/8.1 and Windows 10. The Enigma Protector will make your software resistant to cracking, and thus will increase your sales. The use of attack-proof cryptoalgorithms for registration key generation will make it impossible for others to reconstruct or reproduce the registration key generator for your software. Various methods of code obfuscation, mutation and virtualization will help protect your application from hacking, modifying, disassembling, illegal retrieval of unique functions and data, etc. | |||||||||||||||||||||||||
| Main Benefits | |||||||||||||||||||||||||
| The 'Try Before Buy' Concept | License Manager and Mailer | Virtual Box Technology | Virtual Machine | ||||||||||||||||||||||
| Trial limitations restrict functioning of the application to a certain period of time and once it is expired, the program has to be either uninstalled from the computer or registered (purchased). The Enigma Protector allows you to limit the number of application launches and the number of days that the application can be used since the first launch, to specify the dates of the first and last launch, as well as the time of each run. | License Manager allows you to store and process purchase orders, to generate registration keys and store various customer records in a database. The Mailer allows generating and sending template-based e-mails (for example, messages about a purchase made or a new version available) to registered users. The tools have a user-friendly and simple interface and a wide range of unique features. | The unique technology offers a possibility to consolidate the files used by your application into a single module without loss of efficiency. This function supports all kinds of files – dll, ocx, mp3, avi, etc. Virtual Box will protect your files, and will prevent them from being copied and used in third-party products. | The most powerful and sophisticated mechanism for executable files protection. When a secure module is run, part of the program and protection code is translated (decompiled) into the so-called PCODE (a programming language which can only be read by the Enigma Protector) and the decompiled code is executed in its own virtual processor. Comprehension of such a code is almost impossible, not to mention its modification. | ||||||||||||||||||||||
| Miscellaneous | |||||||||||||||||||||||||
| |||||||||||||||||||||||||